MAD MOBILE SECURITY – OVERVIEW
MAD is an all-in-one platform for the security analysis of Mobile Applications: it performs a fully automated Vulnerability Assessment without OS restrictions: it supports both Android and iOS and its only requirement is the mobile app's package. Thanks to this automation, it can scan the Mobile App, rapidly providing an overview of all releases and related vulnerability trends before they can cause damage. Each scan is quick as well as accurate. MAD was built to be accessible to all kinds of users, from technicians to managers: the reporting engine produces results, which cover both technical aspects and standards compliance. Discover MAD!-
Android & iOS
MAD supports Android & iOS. No source code needed. Just the package.
-
Clear and reliable results.
Results organised in sections: OS statistics, standards compliance and tech area vulnerabilities.
-
Easy to use
MAD is for all users: just upload the mobile app and wait for the results!
-
Cloud & On-Premises
MAD is available via cloud or can be installed on your premises.
MAD AT WORK
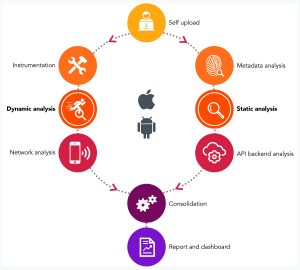
| SELF UPLOAD | |
| The first step provides for the upload of the mobile app package, APK for Android, IPA for iOS. A simple point and click operation: choose the package and upload. | |
| INSTRUMENTATION | METADATA ANALYSIS |
| MAD’s backend instrumentates iOS apps: the package is patched with our code to implement Dynamic Analysis without relying on jailbreak techniques. This operation will not affect performance or behaviour. The new IPA is installed with just one click. | At the same time MAD starts the Metadata Analysis on the package, to find unwanted files and wrong configurations. Manifests, plists and the entire package will be checked. |
| DYNAMIC ANALYSIS | STATIC ANALYSIS |
| During the normal use of the app, MAD collects informations about the sensitive functions of the app, hooking more of 100 of them. Every aspects is under control: URL, IPC, Encryption, Storage, etc. Once completed a tour of the app under analysis, with one tap is possible to upload these informations: MAD’s backend will analyze them. |
Static Analysis takes place entirely on the backend once the package has been uploaded: the app’s code is decompiled and analyzed. The hardcoded password, API keys, deprecated functions and coding patterns will be identified. |
| NETWORK ANALYSIS | API BACKEND ANALYSIS |
| All the network traffic generated by the mobile app is collected and analyzed to check for anomalies and in respect of the best practices, to avoid data exfiltration, stealing of sensitive data and unwanted monitoring. | MAD performs a complete analysis of the app’s backend to identify flaws in property and third parties’ APIs. Also the SDKs used are analyzed, so the entire ecosystem is checked, detecting possible issues from all data sources. |
| CONSOLIDATION | |
| During consolidation MAD brings together the various results and reduces false positives to a minimum as well as improving usability. | |
| REPORT AND DASHBOARD | |
| This last step produces the final result: a complete PDF report and a web dashboard describing the security status of the mobile app. By browsing MAD’s backend it will be possible to see the issues that have been found, discover more about single vulnerability and standards compliance, and monitor the entire security history between various app’s versions. | |
The Benefits of MAD
MAD takes care of your mobile app. Our platform guarantees your mobile app security scans and vulnerability assessments, it’s quick and reliable and uses an engineeristic approach that is also easy to use. Discover MAD's major benefits!1
Speed, Reliability, Security.
The automation provided by MAD assures quick and reliable security scans of your Mobile App. In this way you can keep your assets and data safe without delays.
2
Continuous monitoring over your Mobile App in all aspects. Clear results for all.
MAD keeps track of the entire security history of your mobile app, release by release. MAD covers all aspects and analysis techniques providing clear results for all kinds of user.
3
Standards Compliance.
Standards compliance is very important for your business: MAD is built to ensure an overview about major standards compliance such as PCI DSS, GDPR and OWASP, allowing a rapid remediation.

